Popular Posts
Objective
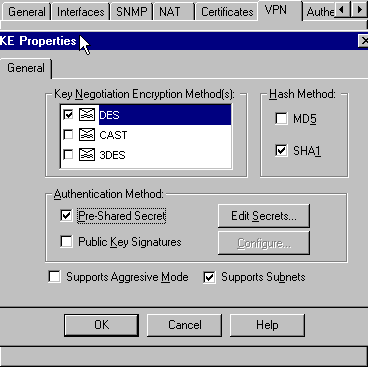
Cisco ASA configurations hide the pre-shared keys for VPN connections. Entering the command \'more system:running-config\' will allow you to view those. Encryption Method. Client VPN uses the L2TP/IP protocol, with the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase2. Meraki Client VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your.
Internet Protocol Security (IPSec) is used to protect communications through the encryption of IP packets during a communication session. IPSec is also an internet protocol used to establish mutual authentication between two endpoints at the beginning of a communication session and negotiation of cryptographic keys during session. Virtual Private Network (VPN) is a private network that allows the transmission of information between two PCs across the network. VPN establishes a high level of security on the private network through the use of encryption.
This document shows the configuration of the IPSec VPN with IKE Preshared Key and Manual Key on a WRVS4400N router.
Applicable Devices
• WRVS4400N
Software Version
• v2.0.2.1
Configuration of IPSec VPN Setup
Step 1. Log into the web configuration utility page and choose VPN > IPSec VPN. The IPSec VPN page opens:
Step 2. Choose an option from the Keying Mode drop-down list.
• IKE with Preshared Key — If you select IKE with Preshared key the automatic key management protocols are used to negotiate key material for SA (Security Association).
• Manual — If you select Manual Key Management no key negotiation is needed. The Manual key is usually used for small environments or for troubleshooting purposes.
Note: Both sides of the VPN Tunnel must use the same key management method.
IPSec VPN Setup with IKE Preshared Key
Step 1. Choose IKE with Preshared Key from the drop-down list of the Keying Mode field.
In the Phase 1 area,
Step 2. Choose 3DES in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets. Only 3DES is supported.
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 3. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest. This is not as secure as SHA1 because it is a broken one-way has algorithm.
• SHA1 — A one-way hashing algorithm that produces a 160-bit digest. This is a more secure has algorithm but is not as fast as MD5.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 4. Choose an option from the Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 5. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. When the time expires, a new key will be renegotiated automatically. The Key Lifetime ranges from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.
In the Phase 2 area,
Step 6. Choose 3EDS in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets, Only 3DES is supported
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 7. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest. This is not as secure as SHA1 because it is a broken one-way hash algorithm.
• SHA1 — A one-way hashing algorithm that produces a 160-bit digest. This is a more secure has algorithm but is not as fast as MD5.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 8. Choose an option from the Prefect Forward Secrecy (PFS) drop-down list.
• Enabled — If PFS is enabled, IKE Phase 2 negotiation will generate a new key material for IP traffic encryption and authentication.
• Disabled —If PFS is disabled, IKE Phase 2 negotiation will not generate a new key material for IP traffic encryption and authentication.
Note: Both sides must have selected the same PFS.
Step 9. Enter the character and hexadecimal value that specifies a key used to authenticate IP traffic in the Preshared Key field.
Step 10. Choose an option from the Group drop-down list.The Diffie-Hellman (DH) group to be used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 11. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. If time expires,a new key will be renegotiated automatically. The Key Lifetime ranges from 1081 to 86400 seconds. The default value for Phase 2 is 3600 seconds.
Step 12. Click the Save to save set up.
IPSec VPN Setup with Manual Key

In the IPSec Setup area,
Step 1. Choose the Manual key from the drop-down list of the Keying Mode field.
In the Phase 1 area,
Step 2. Choose 3DES in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets,Only 3DES is supported.
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 3. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
•MD5 — A one-way hashing algorithm that produces a 128-bit digest.
•SHA1 — A one-way hashing algorithm that produces a 160-bit digest.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 4. Choose an option from the Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 5. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. If time expires, a new key will be renegotiated automatically. The Key Lifetime range from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.

In the Phase 2 area,
Step 6. Choose 3EDS in the Encryption Algorithm field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets, Only 3DES is supported
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 7. Enter the encryption key in the Encryption Key field. Since Encryption Algorithm is 3DES enter 24 ASCII Characters as key in the Encryption Key field.
Step 8. Choose an option from the Authentication Algorithm drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest.
•SHA1 — A one-way hashing algorithm that produces a 160-bit digest.
Step 9. Enter the authentication key in the Authentication Key field. If MD5 algorithm was chosen in authentication algorithm field enter 16 ASCII characters as key, otherwise if SHA1 algorithm was chosen enter 20 ASCII characters as authentication key.
Step 10. Enter the inbound SPI (Security Parameter Index) in the Inbound SPI field.
Step 11. Enter the outbound SPI (Security Parameter Index) in the Inbound SPI field. Download film kartun masha.
The SPI (Security Parameter Index) is carried in the ESP(Encapsulating Security Payload) header. This enables the receiver to select the SA, under which a packet should be processed. The SPI is a 32-bit value. Both decimal and hexadecimal values are acceptable. Each tunnel must have unique an Inbound SPI and Outbound SPI. No two tunnels share the same SPI.
Step 12. Enter the outbound SPI (Security Parameter Index) in the Inbound SPI field.
Note: The Inbound SPI should match with the router Outbound SPI, and vice verse.
Step 13. Click the Save to save set up.
IPSec VPN Status
Step 1. Log in to the web configuration utility, choose VPN > IPSec VPN. The IPSec VPN page opens:
Note: Please make sure a VPN Tunnel is created. Refer to article IPSec VPN Local and Remote Group Setup on WRVS4400N Router on how to do this.
Step 2. Click Advanced. It displays two more options.
• Aggressive mode — Aggressive Mode squeezes the IKE SA negotiation into three packets, with all data required for the SA passed by the initiator. The responder sends the proposal, key material and ID, and authenticates the session in the next packet. The initiator replies by authenticating the session. Negotiation is quicker, and the initiator and responder ID pass in the clear.
• NetBios Broadcast — NetBIOS broadcasts a Name Query packet to the local network on UDP port 137. Every computer on the local subnet processes the broadcast packet. If a computer on the network is configured for the NetBIOS over TCP/IP (NetBT) protocol, the NetBIOS module in the computer receives the broadcast.
Step 3. Click the desired button.
• Connect — Establishes the connection for the current VPN tunnel.
• Disconnect — Breaks the connection for the current VPN tunnel.
• View Log — It displays VPN logs and the details of each tunnel established.
Step 4. Click Save, to save all the changes.
There are many applications which will implement authentication and encryption of network traffic through a separate third party program.
However, the Microsoft operating system can also implement this natively through the configuration of IPSEC. In this article we will look at what IPSEC is and a simple example of implementation.
What is IPSEC?
Internet Protocol Security, or IPSEC is a protocol used to authenticate and encrypt IP communications. This is accomplished through mutual authentication between agents as well as the exchange of cryptographic keys at the beginning of a session.
IPSEC will also allow the addition of IP restrictions and TCP/UDP level encryption to applications which might not otherwise support it. IPSEC utilizes IP Protocol 50 (ESP), IP Protocol 51 (AH), and UDP Port 500.
Implementing IPSEC
In this example, we will set up IPSEC to encrypt communications between two windows machines. The first machine, a windows 2012 server will act as the VPN server.
The second machine, a Windows 10 client, will act as the VPN client. A LT2P IPSEC VPN can exchange either a pre-shared key or a certificate. In this example, we will exchange a pre-shared key.
Setting up the VPN Server
On the Windows 2012 machine, we will need to install the routing and remote access features. To do so, go in to the Server manager, and Add Roles and Features. Choose a role based or feature based installation. Select the local server. Choose to install the following server roles.
Network Policy and Access Services
Network Policy Server
Remote Access
Direct Access and VPN (RAS)
Routing
Once these new features are installed, you will require a snap in to manage them. Open mmc.exe as an administrator. Go to File Add/Remove Snap In. Add the routing and remote access snap in.
This snap in allows the configuration of multi-protocol LAN-to-LAN, LAN-to-WAN, virtual private network (VPN), and network address translation (NAT) routing services.
In the mmc console, right click on routing and remote access and choose to add server. Choose the local machine. Next, right click on the newly created machine and choose Configure and Enable Routing and Remote Access. Choose the Remote Access(Dial Up or VPN).
Then check the VPN option. You must have at least two network cards for this to work. One of them can be a loopback. Specify a range of addresses to be provided for the incoming connection. Make sure they do not conflict with any other addresses allocated on your existing network. In this example, we will not be using a radius server.
Next, attempt to startthe routing and remote access service. The following registry key may need to be deleted to start the service.
In the mmc.exe console, right click on the computer name and go to Properties. Modify those properties on the security tab.
Choose the authentication methods as shown below.
Check the box to allowcustom IPSEC policy for L2TP/IKEv2 connection. Add a pre-shared key.
Finally, you will need to modify a user to be allowed to access the VPN. Open compmgmt.msc, go to Local Users and Groups, and hit properties on the user that you wish to utilize for the VPN.
Go to the Dial Up tab. Choose Allow Access and hit Apply. A reboot will be required on your machine. After the reboot, you will be ready to test your first client.
Setting up the Windows 10 machine
On the Windows 10 machine, open Network and Internet Settings. Choose VPN from the left panel and add a VPN connection. Edit the advanced options.
Place the IP address of your VPN server under server name or address. Choose the L2TP/IPSEC with pre-shared key option under VPN type. Add in the pre-shared key and username and password.
The security properties for the VPN will need to be modified under the network adapter. On the VPN adapter, choose properties, and go to the Security tab. Check the EAP radio button and choose Microsoft: Secured password (EAP-MSCHAPv2)(encryption enabled).
Finally, right click theadapter again to connect. Congratulations! You have created an IPSEC VPNtunnel.
...'>Cisco Vpn Pre Shared Key Decrypt(10.02.2020)Objective
Cisco ASA configurations hide the pre-shared keys for VPN connections. Entering the command \'more system:running-config\' will allow you to view those. Encryption Method. Client VPN uses the L2TP/IP protocol, with the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase2. Meraki Client VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your.
Internet Protocol Security (IPSec) is used to protect communications through the encryption of IP packets during a communication session. IPSec is also an internet protocol used to establish mutual authentication between two endpoints at the beginning of a communication session and negotiation of cryptographic keys during session. Virtual Private Network (VPN) is a private network that allows the transmission of information between two PCs across the network. VPN establishes a high level of security on the private network through the use of encryption.
This document shows the configuration of the IPSec VPN with IKE Preshared Key and Manual Key on a WRVS4400N router.
Applicable Devices
• WRVS4400N
Software Version
• v2.0.2.1
Configuration of IPSec VPN Setup
Step 1. Log into the web configuration utility page and choose VPN > IPSec VPN. The IPSec VPN page opens:
Step 2. Choose an option from the Keying Mode drop-down list.
• IKE with Preshared Key — If you select IKE with Preshared key the automatic key management protocols are used to negotiate key material for SA (Security Association).
• Manual — If you select Manual Key Management no key negotiation is needed. The Manual key is usually used for small environments or for troubleshooting purposes.
Note: Both sides of the VPN Tunnel must use the same key management method.
IPSec VPN Setup with IKE Preshared Key
Step 1. Choose IKE with Preshared Key from the drop-down list of the Keying Mode field.
In the Phase 1 area,
Step 2. Choose 3DES in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets. Only 3DES is supported.
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 3. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest. This is not as secure as SHA1 because it is a broken one-way has algorithm.
• SHA1 — A one-way hashing algorithm that produces a 160-bit digest. This is a more secure has algorithm but is not as fast as MD5.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 4. Choose an option from the Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 5. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. When the time expires, a new key will be renegotiated automatically. The Key Lifetime ranges from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.
In the Phase 2 area,
Step 6. Choose 3EDS in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets, Only 3DES is supported
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 7. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest. This is not as secure as SHA1 because it is a broken one-way hash algorithm.
• SHA1 — A one-way hashing algorithm that produces a 160-bit digest. This is a more secure has algorithm but is not as fast as MD5.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 8. Choose an option from the Prefect Forward Secrecy (PFS) drop-down list.
• Enabled — If PFS is enabled, IKE Phase 2 negotiation will generate a new key material for IP traffic encryption and authentication.
• Disabled —If PFS is disabled, IKE Phase 2 negotiation will not generate a new key material for IP traffic encryption and authentication.
Note: Both sides must have selected the same PFS.
Step 9. Enter the character and hexadecimal value that specifies a key used to authenticate IP traffic in the Preshared Key field.
Step 10. Choose an option from the Group drop-down list.The Diffie-Hellman (DH) group to be used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 11. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. If time expires,a new key will be renegotiated automatically. The Key Lifetime ranges from 1081 to 86400 seconds. The default value for Phase 2 is 3600 seconds.
Step 12. Click the Save to save set up.
IPSec VPN Setup with Manual Key

In the IPSec Setup area,
Step 1. Choose the Manual key from the drop-down list of the Keying Mode field.
In the Phase 1 area,
Step 2. Choose 3DES in the Encryption field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets,Only 3DES is supported.
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 3. Choose an option from the Authentication drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
•MD5 — A one-way hashing algorithm that produces a 128-bit digest.
•SHA1 — A one-way hashing algorithm that produces a 160-bit digest.
Note: Both sides of the VPN endpoints must use the same Authentication method.
Step 4. Choose an option from the Group drop-down list. The Diffie-Hellman (DH) group is used for key exchange.
•768-bit (Group 1) algorithm — This group provides the least level of security and specifies the IPSec to use 768-bit for DH key exchange
•1024-bit (Group 2) algorithm — This group specifies the IPSec to use for 1024-bit for DH key exchange.
•1536-bit (Group 5) algorithm — This group provides the highest level of security to the network and specifies the IPSec to use 1536-bit for DH key exchange.
Note: Group 5 provides the most security whereas the Group 1 the least security.
Step 5. Enter the lifetime (in seconds) of the IKE generated key in the Key LifeTime. If time expires, a new key will be renegotiated automatically. The Key Lifetime range from 1081 to 86400 seconds. The default value for Phase 1 is 28800 seconds.

In the Phase 2 area,
Step 6. Choose 3EDS in the Encryption Algorithm field. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets, Only 3DES is supported
Note: Both sides of the VPN Tunnel must use the same Encryption method.
Step 7. Enter the encryption key in the Encryption Key field. Since Encryption Algorithm is 3DES enter 24 ASCII Characters as key in the Encryption Key field.
Step 8. Choose an option from the Authentication Algorithm drop-down list. Authentication determines a method to authenticate ESP Packets. The user can choose MD5 or SHA1 from the drop-down list.
• MD5 — A one-way hashing algorithm that produces a 128-bit digest.
•SHA1 — A one-way hashing algorithm that produces a 160-bit digest.
Step 9. Enter the authentication key in the Authentication Key field. If MD5 algorithm was chosen in authentication algorithm field enter 16 ASCII characters as key, otherwise if SHA1 algorithm was chosen enter 20 ASCII characters as authentication key.
Step 10. Enter the inbound SPI (Security Parameter Index) in the Inbound SPI field.
Step 11. Enter the outbound SPI (Security Parameter Index) in the Inbound SPI field. Download film kartun masha.
The SPI (Security Parameter Index) is carried in the ESP(Encapsulating Security Payload) header. This enables the receiver to select the SA, under which a packet should be processed. The SPI is a 32-bit value. Both decimal and hexadecimal values are acceptable. Each tunnel must have unique an Inbound SPI and Outbound SPI. No two tunnels share the same SPI.
Step 12. Enter the outbound SPI (Security Parameter Index) in the Inbound SPI field.
Note: The Inbound SPI should match with the router Outbound SPI, and vice verse.
Step 13. Click the Save to save set up.
IPSec VPN Status
Step 1. Log in to the web configuration utility, choose VPN > IPSec VPN. The IPSec VPN page opens:
Note: Please make sure a VPN Tunnel is created. Refer to article IPSec VPN Local and Remote Group Setup on WRVS4400N Router on how to do this.
Step 2. Click Advanced. It displays two more options.
• Aggressive mode — Aggressive Mode squeezes the IKE SA negotiation into three packets, with all data required for the SA passed by the initiator. The responder sends the proposal, key material and ID, and authenticates the session in the next packet. The initiator replies by authenticating the session. Negotiation is quicker, and the initiator and responder ID pass in the clear.
• NetBios Broadcast — NetBIOS broadcasts a Name Query packet to the local network on UDP port 137. Every computer on the local subnet processes the broadcast packet. If a computer on the network is configured for the NetBIOS over TCP/IP (NetBT) protocol, the NetBIOS module in the computer receives the broadcast.
Step 3. Click the desired button.
• Connect — Establishes the connection for the current VPN tunnel.
• Disconnect — Breaks the connection for the current VPN tunnel.
• View Log — It displays VPN logs and the details of each tunnel established.
Step 4. Click Save, to save all the changes.
There are many applications which will implement authentication and encryption of network traffic through a separate third party program.
However, the Microsoft operating system can also implement this natively through the configuration of IPSEC. In this article we will look at what IPSEC is and a simple example of implementation.
What is IPSEC?
Internet Protocol Security, or IPSEC is a protocol used to authenticate and encrypt IP communications. This is accomplished through mutual authentication between agents as well as the exchange of cryptographic keys at the beginning of a session.
IPSEC will also allow the addition of IP restrictions and TCP/UDP level encryption to applications which might not otherwise support it. IPSEC utilizes IP Protocol 50 (ESP), IP Protocol 51 (AH), and UDP Port 500.
Implementing IPSEC
In this example, we will set up IPSEC to encrypt communications between two windows machines. The first machine, a windows 2012 server will act as the VPN server.
The second machine, a Windows 10 client, will act as the VPN client. A LT2P IPSEC VPN can exchange either a pre-shared key or a certificate. In this example, we will exchange a pre-shared key.
Setting up the VPN Server
On the Windows 2012 machine, we will need to install the routing and remote access features. To do so, go in to the Server manager, and Add Roles and Features. Choose a role based or feature based installation. Select the local server. Choose to install the following server roles.
Network Policy and Access Services
Network Policy Server
Remote Access
Direct Access and VPN (RAS)
Routing
Once these new features are installed, you will require a snap in to manage them. Open mmc.exe as an administrator. Go to File Add/Remove Snap In. Add the routing and remote access snap in.
This snap in allows the configuration of multi-protocol LAN-to-LAN, LAN-to-WAN, virtual private network (VPN), and network address translation (NAT) routing services.
In the mmc console, right click on routing and remote access and choose to add server. Choose the local machine. Next, right click on the newly created machine and choose Configure and Enable Routing and Remote Access. Choose the Remote Access(Dial Up or VPN).
Then check the VPN option. You must have at least two network cards for this to work. One of them can be a loopback. Specify a range of addresses to be provided for the incoming connection. Make sure they do not conflict with any other addresses allocated on your existing network. In this example, we will not be using a radius server.
Next, attempt to startthe routing and remote access service. The following registry key may need to be deleted to start the service.
In the mmc.exe console, right click on the computer name and go to Properties. Modify those properties on the security tab.
Choose the authentication methods as shown below.
Check the box to allowcustom IPSEC policy for L2TP/IKEv2 connection. Add a pre-shared key.
Finally, you will need to modify a user to be allowed to access the VPN. Open compmgmt.msc, go to Local Users and Groups, and hit properties on the user that you wish to utilize for the VPN.
Go to the Dial Up tab. Choose Allow Access and hit Apply. A reboot will be required on your machine. After the reboot, you will be ready to test your first client.
Setting up the Windows 10 machine
On the Windows 10 machine, open Network and Internet Settings. Choose VPN from the left panel and add a VPN connection. Edit the advanced options.
Place the IP address of your VPN server under server name or address. Choose the L2TP/IPSEC with pre-shared key option under VPN type. Add in the pre-shared key and username and password.
The security properties for the VPN will need to be modified under the network adapter. On the VPN adapter, choose properties, and go to the Security tab. Check the EAP radio button and choose Microsoft: Secured password (EAP-MSCHAPv2)(encryption enabled).
Finally, right click theadapter again to connect. Congratulations! You have created an IPSEC VPNtunnel.
...'>Cisco Vpn Pre Shared Key Decrypt(10.02.2020)